Sometimes we learn about protocols. Sometimes, we learn from protocols. The latter was the case for me as I set about evaluating various SSL/TLS website and Email test suites.
SSL Online Test Suites
The following three tools actually compliment each other, each providing unique functions not available in the other test suites. It is best to run all three tools against a website to test for compliance, security, compatibility, and vulnerabilities.
♦ SSLTools (http://www.ssltools.com/)
This site provdes a quick “down and dirty” look at your website’s SSL Certificate Chain. It DOES NOT give you any level of detail regarding browser compatibility, Cipher suites, and potential vulnerabilities. Some web browsers will show an error indication if “insecure content” is delivered. This can be problematic for CMS-driven (Content Management System) websites that were converted to SSL. This tool will list that “insecure content“.
♦ SSL Labs (https://www.ssllabs.com/ssltest/)
This site, by Qualsys, provides a detailed breakdown your SSL/TLS website particulars. You can view your certificate’s details. It will list all of the ciphers that your site supports and the protocols that use them (SSLv2, SSLv3, TLS1.0, TLS1.1, and TLS1.2). It tests your website’s protocol for SSL-related exploits. It displays what browsers and O/S systems are compatible with your website. When it is all done, it indicates a Grade (A+ to F). This is the only test available for DNS-based CAA (Certification Authority Authorization) checks. This, from my observations, is the most widely used test site. It DOES NOT test your site for “insecure content” delivery.
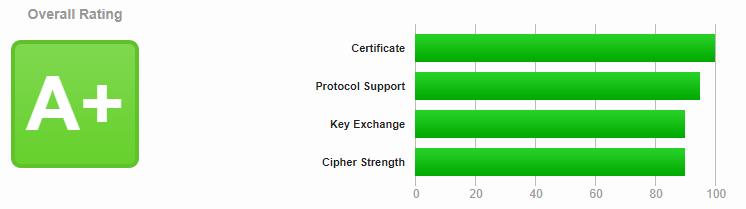
♦ HTBridge (https://www.htbridge.com/ssl/)
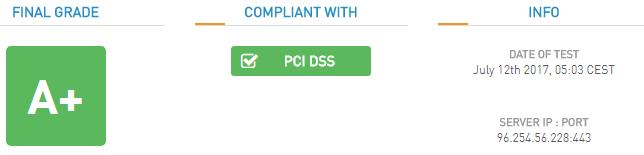
I like this site the most, although it is a real “Ball-Buster”. This site, from High-Tech Bridge, is great for impressing your nerdy friends. Like Qualsys‘ SSLLabs, it returns your Certificate information, tests for potential vulnerabilities, and lists all available Cipher suites for each given SSL/TLS protocol version. It also returns an overall grade (A+ to F) and WILL ALSO indicate compliance with HIPAA, PCI/DSS, and NIST recommendations. It DOES NOT test your site for “insecure content“. The really cool thing about the High-Tech Bridge test is that it can test anything, including your Email services, FTP services, and access portals.
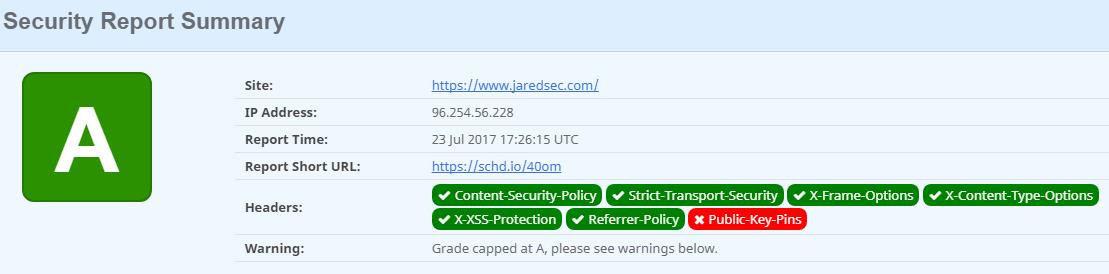
Content Security Checks
There are two excellent sites for checking a website’s Content Security Policy headers. CSP headers have been around for a while now, but their use is getting more common. They tell the browser what to expect from your website, and how data is handled. Clickjacking can be prevented by defining, through “X-Frame-Options” of “frame-src” policies, how your site should be displayed within a iFrame. “X-Content-Type-Options” options tell the browser not to load resources or scripts that do not have a correct MIME type associated with them. If your website does use inline scripts, like Javascript, “X-XSS-Protection” headers prevent a site from loading scripts that are not local to your website, mitiigating Cross-Site Scripting attacks.
♦ SecurityHeaders.io (https://securityheaders.io/)
This is a very fast check of your website’s header information performed by Secarma, a UK-based Pentesting and Cybsersecurity company. It returns an overall grade (A+ to F). It is unique in that it tests for X-WebKit-CSP headers used by older versions of Chrome, Safari, and other WebKit-based browsers.
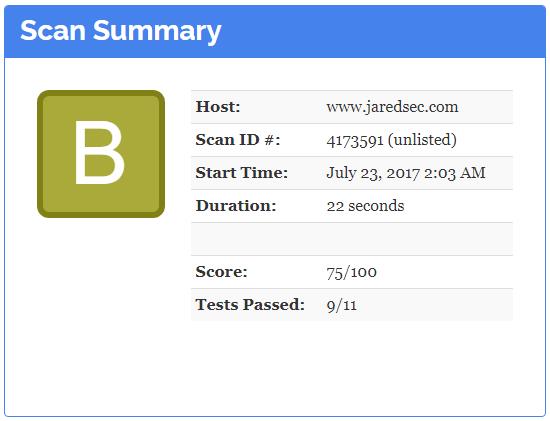
♦ Observatory (https://observatory.mozilla.org/)
This is test suite, by Mozilla, the “Ball-Buster” of CSP (Content Security Policy) checks. It also returns a grade (A+ to F) for your website. It provides the best source of information for the individual headers and how to set them for your site. I think the scoring results may be a little biased against CMS-driven websites (WordPress, Joomla, Drupal, phpBB, etc.), which are powered by scripting. This site forces you to learn about content security and privacy.
Takeaways
- It is becoming necessary to run SSL/TLS on all websites. Come October 2017, Google’s Chrome browser will popup warning messages when sending any form data over an insecure protocol.
- Use and set the HTTP Strict Transport Security (HSTS) header set to a minimum of six months (15768000). This header ensures that a browser will always use HTTPS rather than HTTP protocol. For both Apache 2.2 and 2.4 versions, a sample HSTS header definition looks like: Header add Strict-Transport-Security “max-age=63072000; includeSubdomains”.
- If you seek true compliance with HIPAA and NIST standards, you will need to support the mandatory minimum cipher of “TLS_RSA_WITH_3DES_EDE_CBC_SHA“. OpenSSL’s designation for this cipher is “DES-CBC3-SHA“. This cipher has a key strength of 168 bits, but only an effective key strength of 112 bits. As such, many SSL/TLS test suites will label this cipher as “Weak”. There is a compromise that must be made here.Some OpenSSL implementations on Debian-based distributions like Ubuntu, have removed 3DES entirely from their package. This is not the case with Slack/Suse-based or RedHat/CentOS-based distributions of Linux.
- The DNS CAA (Certification Authority Authorization) record type is still experimental, but it is an easy thing to implement. It will become formally adopted in September 2017. For BIND-type (Berkeley Internet Name Domain) DNS systems, a SOA (Start Of Authority) record might look like this: IN CAA 0 issue “letsencrypt.org”. A wildcard host entry might look like this: @ 3600 IN CAA 0 issue “letsencrypt.org”.
- You can use Google’s Chrome browser to check your settings (Settings -> More tools -> Developer tools). Security Policy errors from the content on your site will be listed in red in the Content window.
- SSL Certificates can be had for the low, low cost of free! After 1.5 years since Beta, and one year of operation, Letsencrypt has doles out 100 million certificates, protecting somewhere between 17 million and 46 million websites. You can view the Electronic Frontier Foundation’s (EFF) report here. However, Comodo also provides free certificates as well.
- Set a “X-Content-Type-Options” options to a value of: “nosniff’ like ths example (Apache 2.2 and 2.4):
Header add X-Content-Type-Options “nosniff”. This ensures that resources loaded are set by valid MIME types. - Set a strong Referrer Policy. Your website will leak customer-oriented metadata every time a referral is made to an external source. This policy helps protect your customers’ privacy. An Apache 2.2 and 2.4 policy might look like this: Header add Referrer-Policy “strict-origin-when-cross-origin”.
- Set and use a “OCSP Stapling” (Online Certificate Status Protocol) header. Since OCSP requires the browser to contact the CA to confirm certificate validity it compromises privacy, the CA knows what website is being accessed and who accessed it. Setting this header reduces the traffic load to the CA and helps mitigate DDoS attacks against the CA. Privacy is enhanced because the client information is not passed to the CA. This feature is not available on Apache 2.2 but ins available on Apache 2.4 through a configuration directive: SSLUseStapling on.
- Remember to test other SSL/TLS-based servers that you might support, like POP3, IMAP, SMTP, and FTP services. The same vulnerabilities (BEAST, CRIME, POODLE, SWEET32, etc) can exist there as well.