The Nay Sayers
Trolling through articles released this week, I came across a review of Lockheed Martin’s “Cyber Kill Chain” that was written by CSO Online: https://www.csoonline.com/article/2134037/cyber-attacks-espionage/strategic-planning-erm-the-practicality-of-the-cyber-kill-chain-approach-to-security.html on 11/7/2017. I found the article to be somewhat disingenuous. The CSO Online article was more of a rehash of a Dark Reading article: https://www.darkreading.com/attacks-breaches/deconstructing-the-cyber-kill-chain/a/d-id/1317542? written on 11/18/2014. “We’re not afraid to say it: Over-focus on the Cyber Kill Chain can actually be detrimental to network security. Why? Because the Cyber Kill Chain model, as sexy as it is, reinforces old-school, perimeter-focused, malware-prevention thinking. And the fact is that intrusion prevention solutions cannot provide 100% protection. A persistent, highly determined, and highly skilled attacker will always find a way in. And once the attacker is past your perimeter, traditional Cyber Kill Chain-style prevention solutions like firewalls, sandboxes, and antivirus can’t help. Once they’ve bypassed these solutions, attackers are free to operate in your network unobstructed.”
The Cyber Kill Chain Illustrated
Every IT Security professional probably already has a copy of this on their bulletin board, but it is presented below for review:

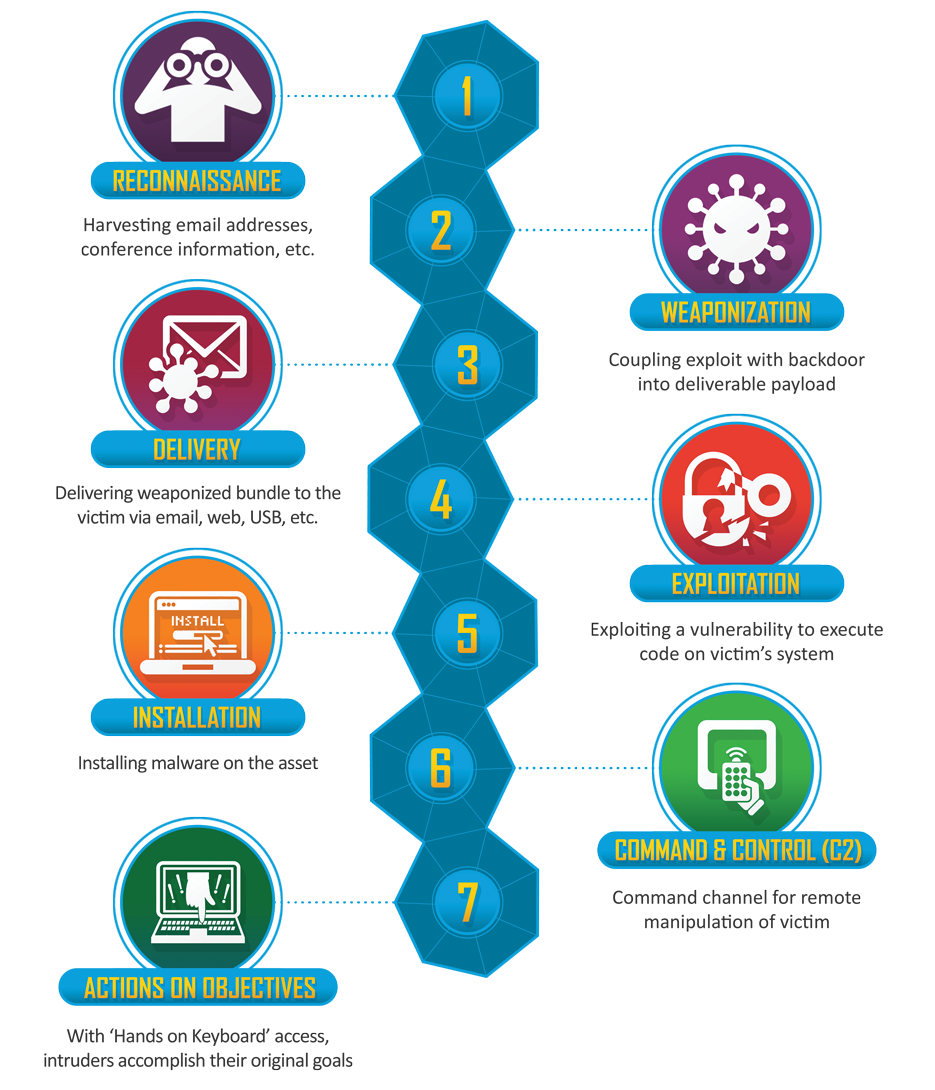
The Original Work
Lockheed Martin’s original PDF on the matter was published on 10/24/2010 by three individuals specifically targeting APT actors, where Cyber attacks are part of a larger campaign:
- Eric M. Hutchins
- Michael J. Cloppert
- Rohan M. Amin, Ph.D
The original paper can be found here: ahttps://www.lockheedmartin.com/content/dam/lockheed/data/corporate/documents/LM-White-Paper-Intel-Driven-Defense.pdf.
The whitepaper presents some mitigation techniques in the table included below:
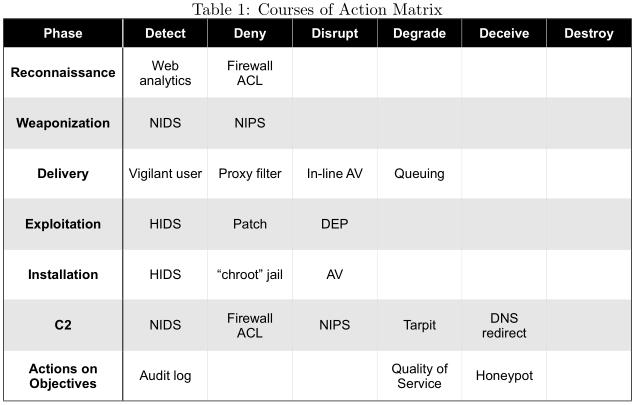
The whitepaper also provides some relevant examples, centered around phishing attacks.
Applicability Today
There are those today that criticize the Cyber Kill Chain, citing that it doesn’t apply to today’s metrics. And to their credit, on page 4 of the PDF White Paper is the statement “This is an integrated, end-to-end process described as a “chain” because any one deficiency will interrupt the entire process“.
I view the illustration not as sequential steps, but as actions that a hacker may, or may not, take. For example, in the case of the Equifax hack, a Host Intrustion Detection System (HIDS) could have detected the intrusion much sooner. Consider that the core pages that actually served Apache Struts information probably don’t change that often. How difficult would it have been to monitor that content?
Today’s network security is an extremely dynamic cat and mouse game.
There is no “magic bullet” for security.